Whose Fault?
Wednesday 11th July, 2007 13:51 Comments: 1
I saw this when it first appeared on the SecurityFocus mailing list. A vulnerability has been discovered (complete with PoC), which (ab)uses the relationship between IE and Firefox. The exploit is quite effective, but there's just as much controversy over who is actually at fault. Instinctively, I say Mozilla. There are two reasons for this:
Jesper Johansson, a former senior security strategist for Microsoft, said in a blog entry: "This exploit is actually for Firefox, but Thor exploited it by making IE launch Firefox" and "Firefox fails to properly validate the parameters, and any fix will have to come from Mozilla, not Microsoft".
The Register said: Roger Thompson, CTO of Exploit Prevention Labs, says Microsoft shares culpability because IE fails to properly validate the input before passing it along. "I think it's an IE issue mostly, because if you access the exploit directly with Firefox, FF warns you that something bad is happening and advises you to not do it," he said in an instant message.
But I think that's wrong. It would be nice if IE validated the input, but I don't think it should necessarily be expected to validate everything. The third party application should be the one validating all input.
Most importantly, if you try and run the PoC under a default installation of Vista (with UAC and Protected Mode enabled), just like Firefox, it warns you that something bad might be about to happen (unless you previously told IE that it could trust the third party application "Firefox"), so Vista users have ways to mitigate bad things from happening.
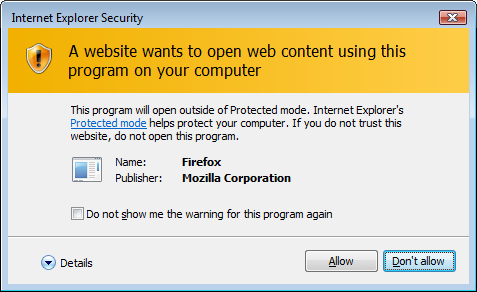
EDIT: It seems that Firefox is the current attack vector but IE is to blame for not escaping quote characters when passing on the input to the command line. Firefox could have registered its URL handler with pure DDE instead and avoided the possibility of a command line argument injection, but it would be best if IE made it safe to launch external applications. The exploitability on those depend on what arguments each application accepts. If Firefox is already running then IE doesn't instantiate it through the command line, but through DDE instead, so the exploit doesn't work.
- Firefox does not validate external input
- Firefox registers the "firefoxurl" URI
Jesper Johansson, a former senior security strategist for Microsoft, said in a blog entry: "This exploit is actually for Firefox, but Thor exploited it by making IE launch Firefox" and "Firefox fails to properly validate the parameters, and any fix will have to come from Mozilla, not Microsoft".
The Register said: Roger Thompson, CTO of Exploit Prevention Labs, says Microsoft shares culpability because IE fails to properly validate the input before passing it along. "I think it's an IE issue mostly, because if you access the exploit directly with Firefox, FF warns you that something bad is happening and advises you to not do it," he said in an instant message.
But I think that's wrong. It would be nice if IE validated the input, but I don't think it should necessarily be expected to validate everything. The third party application should be the one validating all input.
Most importantly, if you try and run the PoC under a default installation of Vista (with UAC and Protected Mode enabled), just like Firefox, it warns you that something bad might be about to happen (unless you previously told IE that it could trust the third party application "Firefox"), so Vista users have ways to mitigate bad things from happening.

EDIT: It seems that Firefox is the current attack vector but IE is to blame for not escaping quote characters when passing on the input to the command line. Firefox could have registered its URL handler with pure DDE instead and avoided the possibility of a command line argument injection, but it would be best if IE made it safe to launch external applications. The exploitability on those depend on what arguments each application accepts. If Firefox is already running then IE doesn't instantiate it through the command line, but through DDE instead, so the exploit doesn't work.
I liked Jesper's analysis of Firefox: http://msinfluentials.com/blogs/jesper/archive/2007/07/20/hey-mozilla-quotes-are-not-legal-in-a-url.aspx
It seems that Firefox doesn't escape URLs, even though it blames IE for not escaping them.
It seems that Firefox doesn't escape URLs, even though it blames IE for not escaping them.