Apple
Wednesday 31st January, 2007 09:41 Comments: 5
The Month of Apple Bugs is nearly over (I presume there will be one more later today), and today's was a bumper size:
Multiple developers of Apple based software including Apples own developers seem to have a misunderstanding of how to properly use NSBeginAlertSheet, NSBeginCriticalAlertSheet, NSBeginInformationalAlertSheet, NSGetAlertPanel, NSGetCriticalAlertPanel, NSGetInformationalAlertPanel, NSReleaseAlertPanel, NSRunAlertPanel, NSRunCriticalAlertPanel, NSRunInformationalAlertPanel, and NSLog. For the sake of lulz alone a montage must ensue...
And if you visit the page with more details you'll hear the montage song from Team America.
I'm still not sure how happy I am with some of the full disclosure tactics with these Month of X Bugs projects. I'm okay with full disclosure if other people are exploiting that vulnerability in the wild and there's therefore nothing to hide, or if the developer is known to consistently ignore/take forever to fix vulnerabilities in their products. Apple falls into an odd category, they've never been too horrendous at patching software, but they tend to do it a bad way. They've only recently formed a decent process, and a lot of the communication is still done via their PR section (who often don't have a clue what is going on). Apple also seem to push how flash and funky and secure OSX is compared to Windows, yet throughout the MoKB there were far more problems with Apple and Linux than there were for Windows (IIRC the Windows one didn't even apply to 2003 or Vista). AFAIK Apple have only fixed one of the bugs from the MoAB project (a simple fix, but it still took them more than 3 weeks), but Windows users cannot download that version - you have to download a vulnerable version and then use the software updater to get the secure version. I tried it on my machine the other day and - perhaps because I wasn't paying attention - inadvertently installed iTunes!
Whenever I download software I make sure I don't install things like Google Toolbar, Google Desktop Search, iTunes, MSN Toolbar. This generally means looking out for those checkboxes (especially Google ones), and in the case of QuickTime I choose the version that doesn't install iTunes* - I gave away my 10GB iPod to my brother, I don't plan on buying anything from iTunes if I can't play it back on other devices.
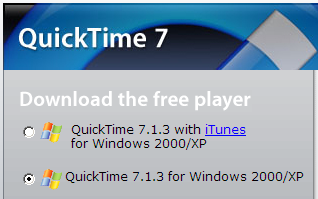
So when I used Apple's software update program I (apparently foolishly) expected it to update the software that I had installed. I did not expect iTunes to magically appear in my Start Menu and my QuickLaunch toolbar. Perhaps it got confused because I was using Windows XP and it "accidentally" installed the "with iTunes" version. Just like how Apple accidentally wrote all the other bugs in their software.
* more specifically, last time I checked, the "QuickTime with iTunes" software is actually just the iTunes setup file that happens to include QuickTime
Multiple developers of Apple based software including Apples own developers seem to have a misunderstanding of how to properly use NSBeginAlertSheet, NSBeginCriticalAlertSheet, NSBeginInformationalAlertSheet, NSGetAlertPanel, NSGetCriticalAlertPanel, NSGetInformationalAlertPanel, NSReleaseAlertPanel, NSRunAlertPanel, NSRunCriticalAlertPanel, NSRunInformationalAlertPanel, and NSLog. For the sake of lulz alone a montage must ensue...
And if you visit the page with more details you'll hear the montage song from Team America.
I'm still not sure how happy I am with some of the full disclosure tactics with these Month of X Bugs projects. I'm okay with full disclosure if other people are exploiting that vulnerability in the wild and there's therefore nothing to hide, or if the developer is known to consistently ignore/take forever to fix vulnerabilities in their products. Apple falls into an odd category, they've never been too horrendous at patching software, but they tend to do it a bad way. They've only recently formed a decent process, and a lot of the communication is still done via their PR section (who often don't have a clue what is going on). Apple also seem to push how flash and funky and secure OSX is compared to Windows, yet throughout the MoKB there were far more problems with Apple and Linux than there were for Windows (IIRC the Windows one didn't even apply to 2003 or Vista). AFAIK Apple have only fixed one of the bugs from the MoAB project (a simple fix, but it still took them more than 3 weeks), but Windows users cannot download that version - you have to download a vulnerable version and then use the software updater to get the secure version. I tried it on my machine the other day and - perhaps because I wasn't paying attention - inadvertently installed iTunes!
Whenever I download software I make sure I don't install things like Google Toolbar, Google Desktop Search, iTunes, MSN Toolbar. This generally means looking out for those checkboxes (especially Google ones), and in the case of QuickTime I choose the version that doesn't install iTunes* - I gave away my 10GB iPod to my brother, I don't plan on buying anything from iTunes if I can't play it back on other devices.

So when I used Apple's software update program I (apparently foolishly) expected it to update the software that I had installed. I did not expect iTunes to magically appear in my Start Menu and my QuickLaunch toolbar. Perhaps it got confused because I was using Windows XP and it "accidentally" installed the "with iTunes" version. Just like how Apple accidentally wrote all the other bugs in their software.
* more specifically, last time I checked, the "QuickTime with iTunes" software is actually just the iTunes setup file that happens to include QuickTime
 Yamahito - Wednesday 31st January, 2007 12:59
Yamahito - Wednesday 31st January, 2007 12:59 The full disclosure in security argument has been going on for many years. I remember Matt Blaze (who amongst other things hosts halfbakery.com, where I used to moderate) posting a transcript of an argument from the 17th century mailing list for locksmiths, and apart from a few technical terms and archaisms, it could be applied almost word for word to modern-day internet security.
My position would be if in doubt, disclose. You don't know which of these bugs may be planned for, and the worst you can say about it is that it forces the developers' hands in making security fixes.
My position would be if in doubt, disclose. You don't know which of these bugs may be planned for, and the worst you can say about it is that it forces the developers' hands in making security fixes.
I definitely think it's better to tell people than sell it on eBay to the highest bidder (who will probably use it for financial gain), but occasionally you see people disclose things without making any effort to contact the developer so they have time to create a patch, which might put a lot more people at risk. I tend to prefer full disclosure when someone provides a workaround or solution at the same time, but that's not always possible, especially with closed source software.
On the other hand, if you don't fully disclose, you can get mobbed and accused of scaremongering - look at the wireless driver issue that was supposed to affect, amongst others, apple - the guys who found the 'flaw' were crucified.
Ok, there were other issues in that case - mainly some bad choice of terms and some responsibilities assigned too early - but still, crucified...
Ok, there were other issues in that case - mainly some bad choice of terms and some responsibilities assigned too early - but still, crucified...
You mean the fact they told everyone they could hack into OSX, which turned out to be a vulnerability in a third party driver (rather than the one that ships), then claimed that the same flaws were resident in the default Macbook wireless device drivers and that those drivers were identically exploitable and Apple had leaned on them not to make this an issue about the Mac drivers because they hadn't fixed the problem, then - apparently, the page on their site has now been removed so I can't confirm this - admitted they'd lied (although Apple did release an updated driver a month later, which I believe fixed two separate stack buffer overflows that could lead to code execution with root privileges)?
Vulnerabilities in third party wireless cards have been around for ages, they could have just as easily attacked a Windows box, but for publicity they chose Apple because of the "Mac user base aura of smugness on security". Their decision to attack Apple was scaremongering, as they wouldn't tell anyone which third party driver was the culprit.
The MoKB guys didn't make a big song and dance about the Apple Airport driver provided with Orinoco-based Airport cards (1999-2003 PowerBooks, iMacs), which was vulnerable to a remote memory corruption flaw that could lead to arbitrary code execution: http://projects.info-pull.com/mokb/MOKB-01-11-2006.html (although it did require the card be placed into active scanning mode).
With Apple, a hole is discovered and they either refuse to discuss the issue or they say they're "looking into the issue" and then refuse to say anything else until it has properly reviewed. They eventually produce a fix, release it along with a whole bunch of other patches, and hope no one notices due to the bare minimum of information. To give an example, eEye complained back in March that it told Apple of a critical vulnerability 153 days earlier but it still hadn't been patched. Back in March 2004 @stake reported holes in OSX to Apple. The US government produced its own advisory on the issue. The UK government produced an advisory. Apple finally put up a notice on an alerts page, but did not inform users.
Vulnerabilities in third party wireless cards have been around for ages, they could have just as easily attacked a Windows box, but for publicity they chose Apple because of the "Mac user base aura of smugness on security". Their decision to attack Apple was scaremongering, as they wouldn't tell anyone which third party driver was the culprit.
The MoKB guys didn't make a big song and dance about the Apple Airport driver provided with Orinoco-based Airport cards (1999-2003 PowerBooks, iMacs), which was vulnerable to a remote memory corruption flaw that could lead to arbitrary code execution: http://projects.info-pull.com/mokb/MOKB-01-11-2006.html (although it did require the card be placed into active scanning mode).
With Apple, a hole is discovered and they either refuse to discuss the issue or they say they're "looking into the issue" and then refuse to say anything else until it has properly reviewed. They eventually produce a fix, release it along with a whole bunch of other patches, and hope no one notices due to the bare minimum of information. To give an example, eEye complained back in March that it told Apple of a critical vulnerability 153 days earlier but it still hadn't been patched. Back in March 2004 @stake reported holes in OSX to Apple. The US government produced its own advisory on the issue. The UK government produced an advisory. Apple finally put up a notice on an alerts page, but did not inform users.
I'd prefer to think of them as inaccuracies rather than lies, brought about by trying to 'dumb down' the story. But the point is that they never demonstrated the flaw with the macbooks. If they had, they wouldn't have had the flack they had.
Apple leaning on them not to disclose could also be a bad thing, I think. There also is certainly a "user base aura of smugness on security," often on the part of people who don't understand /why/ apple/unix is slightly more secure than windows, or that there are certain very real security flaws in *any* OS. Although saying so in such terms was stupid - real shoot-self-foot thinking.
Point is, a bit more disclosure of apple flaws would probably be a good thing if it encouraged them to be a bit more helpful in their attitude to security flaws. But apple does two things very very well - one is GUI design, and the other is marketing.
Apple leaning on them not to disclose could also be a bad thing, I think. There also is certainly a "user base aura of smugness on security," often on the part of people who don't understand /why/ apple/unix is slightly more secure than windows, or that there are certain very real security flaws in *any* OS. Although saying so in such terms was stupid - real shoot-self-foot thinking.
Point is, a bit more disclosure of apple flaws would probably be a good thing if it encouraged them to be a bit more helpful in their attitude to security flaws. But apple does two things very very well - one is GUI design, and the other is marketing.